Which of the Following May Indicate a Malicious Code Attack
Updated 1222020 92456 PM. Expert answeredhoudPoints 400 Log in for more information.
Malicious Code And Malware How To Detect Remove And Prevent
They can damage or compromise digital files erase your hard drive andor allow hackers access to your PC or mobile from a remote location.

. The hacker encrypts and holds your data hostage and then demands a. There are four primary types of attacks they are. Indicate how you would defend the attack from recurring on a network you control.
In an attempt to avoid detection by signature-based antivirus software packages polymorphic viruses modify their own code each time they infect a system. Malicious code is part of a software system or script intended to cause some undesirable effect such as a security breach or direct damage to a system. The code cannot be efficiently controlled by conventional antivirus software alone and it can take a number of forms.
A DLL injection attack occurs when a program is forced to load a dynamic-link library DLL. Trojan horse A program that appears to do something non- malicious. All of the following are examples of malicious code except.
Malwarebytes regards browser hijacker malware to be among the top ten malware attacks targeting businesses today. Which of the following is a practice that helps to prevent the download of viruses and other malicious code when checking your email. Malicious code can take the form of.
In terms of well-known examples of these attacks the following are a handful of the most notable. Which of the following may indicate a. Indicate how you would defend the attack from recurring on a network you control.
Delete or corrupt data website servers etc. This compromises the security of the software because it may be possible to inject malcode into runtime memory. Java Applets ActiveX Controls Scripting languages Browser plug-ins Pushed content Once inside your network or workstation malicious code can enter.
The attacker copies a number of sites that have high website visitors and injects malicious code. What advanced virus technique modifies the malicious code of a virus on each system it infects. Modify data unpermitted encryption weaken security etc.
Obtain data account credentials personal information etc. Each type of malicious code attack can wreak havoc on a defenseless IT infrastructure very quickly or wait on servers for a predetermined amount of time or a trigger to activate the attack. Asked 1222020 21521 PM.
Here are the 15 most common types of Internet security issues or web security problems and some relevant steps you can take to protect yourself your data and your business. It occurs when a program writes data outside the boundary of its allocated memory. Malicious code includes viruses trojan horses worms macros and scripts.
Be aware of the network you are using when connecting a personal unauthorized device. Users visit compromised sites and their browsers run dangerous injected code 3. Use a classified network for all work especially unclassified processing.
Malicious code is code causing damage to a computer or system. Malicious code may manifest itself in a variety of ways and has been quite prevalent in the past. You may use the Internet for research.
It searched for unprotected administrative shares on the local network exploited zero day vulnerabilities in Windows Server and Print Spooler services connected to systems using a default database password or spread by infected USB drive. Malicious code can either activate itself or be like a virus requiring a user to perform an action such as clicking on something or opening an email attachment. Label all files removable media and subject headers with appropriate classification markings.
Select a well-known virus or malicious code attack and write a summary report explaining what kind of malicious attack it was how it spread and attacked other devices and how it was mitigated. When the user views the web page the malicious scripts run allowing the attacker to capture information or perform other actions. Rabbit A worm or virus that reproduces itself without limit in order to exhaust some resource.
The malicious code scans the victims system looks for vulnerabilities and extracts the results to other malicious servers via POST 4. Keyloggers also known as system monitoring or keystroke loggers are malware types created to monitor and record all the keystrokes on an infected computers keyboard. This answer has been confirmed as correct and helpful.
Up to 20 cash back Malicious code is the kind of harmful computer code or web script designed to create system vulnerabilities leading to back doors security breaches information and data theft and other potential damages to files and computing systems. It is code not easily or solely controlled through the use of anti-virus tools. Denial of Service Worms Viruses and Trojan Horses Reconnaissance Reconnaissance attack is a kind of information gathering on network system and services.
Concerns in a triage fashion A simple customer complaint about a sluggish system or unusual user interface behavior may be enough to indicate the. A highly sophisticated worm that was discovered in 2010. Its a type of threat that may not be blocked by antivirus software on its own.
Up to 20 cash back Once a targeted device or system is exposed to malicious code the resulting attack may include unauthorized attempts of any of the following. Do not access links or hyperlinked media such as buttons and graphics in email messages. Viruses Programs that can spread malicious code to other programs by modifying them.
Malicious Code Examples of Buffer Overflow Buffer overflow is a well-known security vulnerability. 3 Malicious Code Malicious code can be spread by downloading corrupted email attachments and files or visiting infected websites. Types of Malicious code.
The goal of a ransomware attack is to gain exclusive control of critical data. This enables the attacker to discover vulnerabilities or weaknesses on the network. Industry studies have revealed that detection of malicious code often takes weeks or months before the damage is noticed and threats are defeated.
Assignment Requirements Select a well-known virus or malicious code attack and write a summary report explaining what kind of malicious attack it was how it spread and attacked other devices and how it was mitigated. You may use the Internet for research. Worm A virus that spreads over a network and can run independently.
Adding to the complexity of cybersecurity is malicious code.
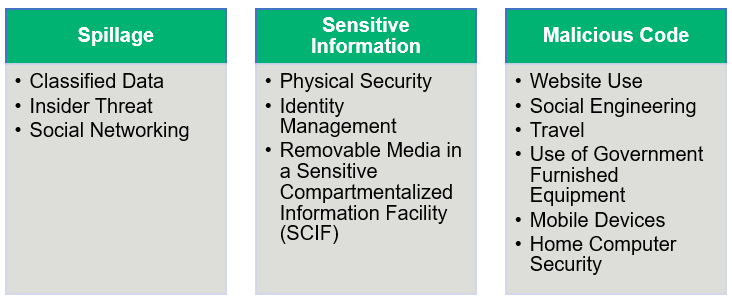
Dod Cyber Awareness Challenge 2020 Your Ultimate Guide Infosec Insights

New Android Flaw Affecting Over 1 Billion Phones Energy Technology Latest Technology News Cyber Security

Infographic Important Tips To Avoid Phishing Attacks Cyber Security Awareness Computer Security Cyber Security

Developing Petya Ransomware Attack Goes Global Targets Merck In Us Cyber Security Cyber Attack Wordpress Security
No comments for "Which of the Following May Indicate a Malicious Code Attack"
Post a Comment